
Create AI videos with 230+ avatars in 140+ languages.
Cybersecurity is serious business, and it's especially important to make sure your team is well-trained in how to protect your company's data. 🥷
But learning all the ins and outs of cyber security can be daunting, and it's not always easy to stay on top of the latest threats.
👉🏻 That's where personalized cybersecurity training videos come in handy.
By creating custom videos that focus on the specific risks your company faces, you can make sure your team is learning the right information in a way that is engaging and easy to remember.
So if you're looking for a way to help your team stay safe online, read on for tips on how to create customized cybersecurity training videos using AI.
What is cybersecurity training?
Cybersecurity training helps organizations and individuals protect themselves from cyber criminals and hackers.
The training covers a variety of topics, including
- how to identify and prevent cyber attacks
- how to respond to an attack
- how to recover from an attack.
Hackers are constantly evolving their methods, so it is important for people to stay up-to-date on the latest cybersecurity threats and how to protect themselves.
Organizations should provide cybersecurity training for all their employees, as it can help to reduce the risk of cyberattacks.
5 common types of cybersecurity training
Before we get into making the video, let's go through the many different types of cybersecurity training:
1. Phishing simulations 🐟
During phishing simulations, employees are taught how to identify and avoid phishing emails.
Phishing is a type of online fraud where criminals try to trick you into giving them personal or financial information.
They may send phishing emails that look like they're from a legitimate company, or they may set up a fake website that looks identical to a real one.
2. Social engineering awareness 🔨
Social engineering awareness refers to teaching employees how to identify and avoid social engineering attacks.
Social engineering is the process of manipulating people into divulging sensitive information or carrying out an action that they wouldn’t normally do. This can be done in person, over the phone, or online.
3. Malware removal training 💾
This type of training teaches employees how to identify and remove malware from their computer systems.
Malware is a type of malicious software that can damage or disable computers, and businesses need to protect themselves from it.
4. Awareness of ransomware attacks 💰
Awareness of ransomware attacks, teaching employees how to protect themselves from this increasingly common type of attack.
Ransomware is a type of malware that encrypts your files and holds them hostage until you pay a ransom.
5. Password management training 🔑
A strong password is the first line of defense against unauthorized access to accounts and data.
By teaching employees how to create and manage strong passwords, you can help to protect your company's information and reputation.
Password management training can cover several topics, including:
- password policies
- creating strong passwords
- storing passwords securely
- using two-factor authentication.
No matter what type of security awareness training you choose, it's important to make sure that it is engaging and relevant to your employees. Only then will they be able to learn the necessary skills to keep your business safe from cyber threats.
And how do we make such a serious topic engaging?
Through video, of course! 📹
4 benefits of using video in cybersecurity training
Cybersecurity training can come in many shapes and forms, from written articles and manuals to in-person lectures.
One particular type strikes a great balance between being more engaging than text, but less laborious than in-person lectures - instructional videos.
Here's why 👇
1. Employees are more likely to pay attention to video content than text-based training
It's no secret that people tend to zone out when they're asked to sit through a long, text-based training session.
After all, who wants to read page after page of dry, boring material? 🥱
Videos, on the other hand, are much more engaging and visually stimulating. Studies have shown that viewers retain 95% of a video's message vs. 10% of text-based messaging.
For example, wouldn’t you rather watch this introduction to a cybersecurity training course instead of reading a training manual? 👇
2. Videos can be used to demonstrate how to complete specific tasks
There's nothing quite like seeing something being done to understand how it's done.
Many people find that watching a video is much more helpful than reading instructions, as it allows them to see the process in action.
Videos, and in particular screen recordings, are perfect to demonstrate step-by-step instructions.
3. Videos can help employees learn the principles of cybersecurity in a fun and engaging way
Learning complex concepts can be difficult, and boring lectures are often quickly forgotten.
That's where videos come in. 🦸♀️
Videos are more visually stimulating than text. They can include graphics, animation, and even video footage to capture your attention.
Besides, videos are usually shorter than written articles, making them easier to consume in one sitting.
Best of all, they can be accessed from anywhere at any time, making them a convenient way to brush up on key concepts.
4. Videos can be used as part of a blended learning approach
We don't advocate for replacing all parts of your training program with a video lesson collection - video just isn't the perfect way of distributing every type of content.
However, using videos as part of your cybersecurity training program can be a great way to mix up different types of content for a more blended approach.
5. Videos are easy to make
This might be the opposite of what you've heard, but yes, videos are now easier to make than ever.
And no, just because they're easy to make, doesn't mean the quality is compromised.
With modern AI training video makers, you can type in some text, and get a video with an (almost) human AI presenter and AI narration.
All without using cameras, microphones, actors, or editing equipment.
Let us show you how it's done. 👇
How to make a security awareness training video in 5 easy steps
To create our video lesson on cybersecurity, we will be using an AI video maker called Synthesia.
The general steps outlined below can be applied to most online video makers though (minus the AI part 😉).
You can also go through the steps in a video format, if you're a visual learner:
Step 1: Create a video script
The first step in any type of video creation is to write a script.
This will help you organize your thoughts and ensure that your video is informative and engaging.
When writing your script, keep in mind that you're trying to educate users about cybersecurity risks and how they can protect themselves. As such, your script should be clear and concise.
If you want to know how to write a video script, we've got a guide that will show it all.

Step 2: Select a video template or start from scratch
Next, head to your video maker of choice, and find a video template that fits the topic of your video.
Or start from scratch, if you'd rather design your own video.
With video templates, you can save time and focus on the content of the training video instead of the design.
To start off with a template in Synthesia, go to 'Templates' in your dashboard, choose the one you like and click on 'Create video'.
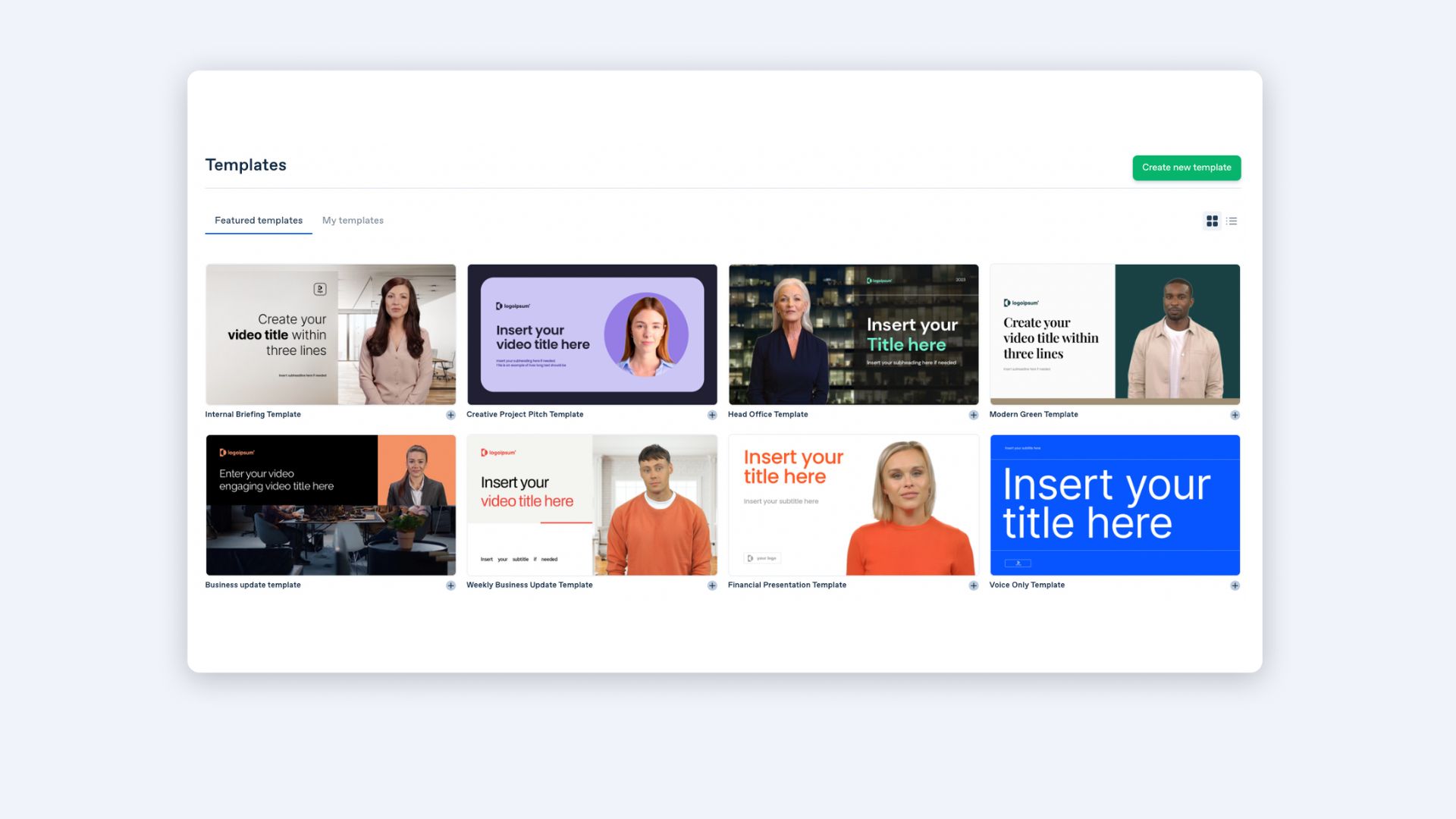
Step 3: Paste text and choose a voice
Remember your video script from step #1?
Take that script, and paste it into the video canvas slide by slide.
Synthesia will analyze that text, and transform it into an AI voiceover in seconds.
So there's no need to record a separate voiceover or hire a voice actor!
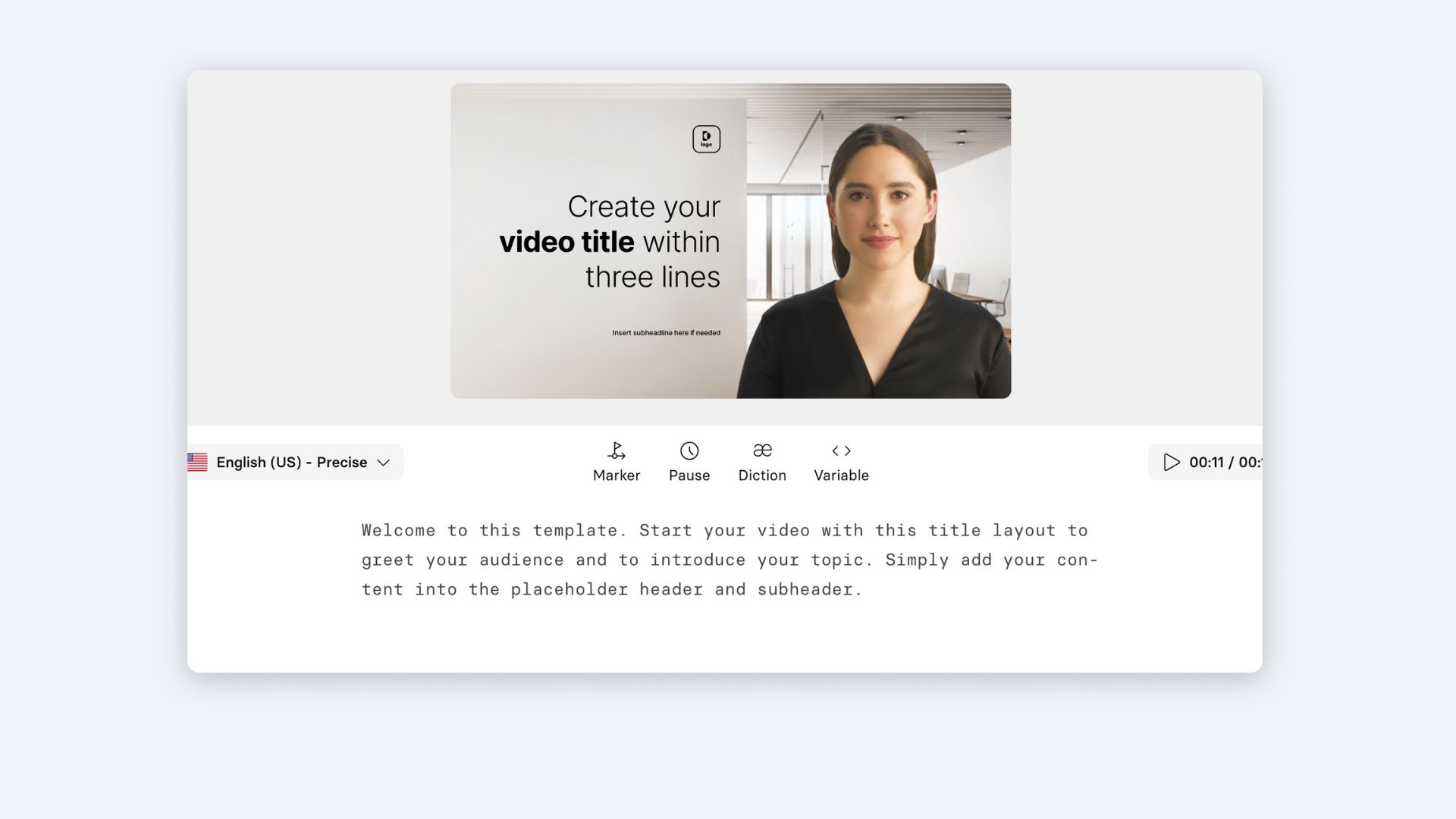
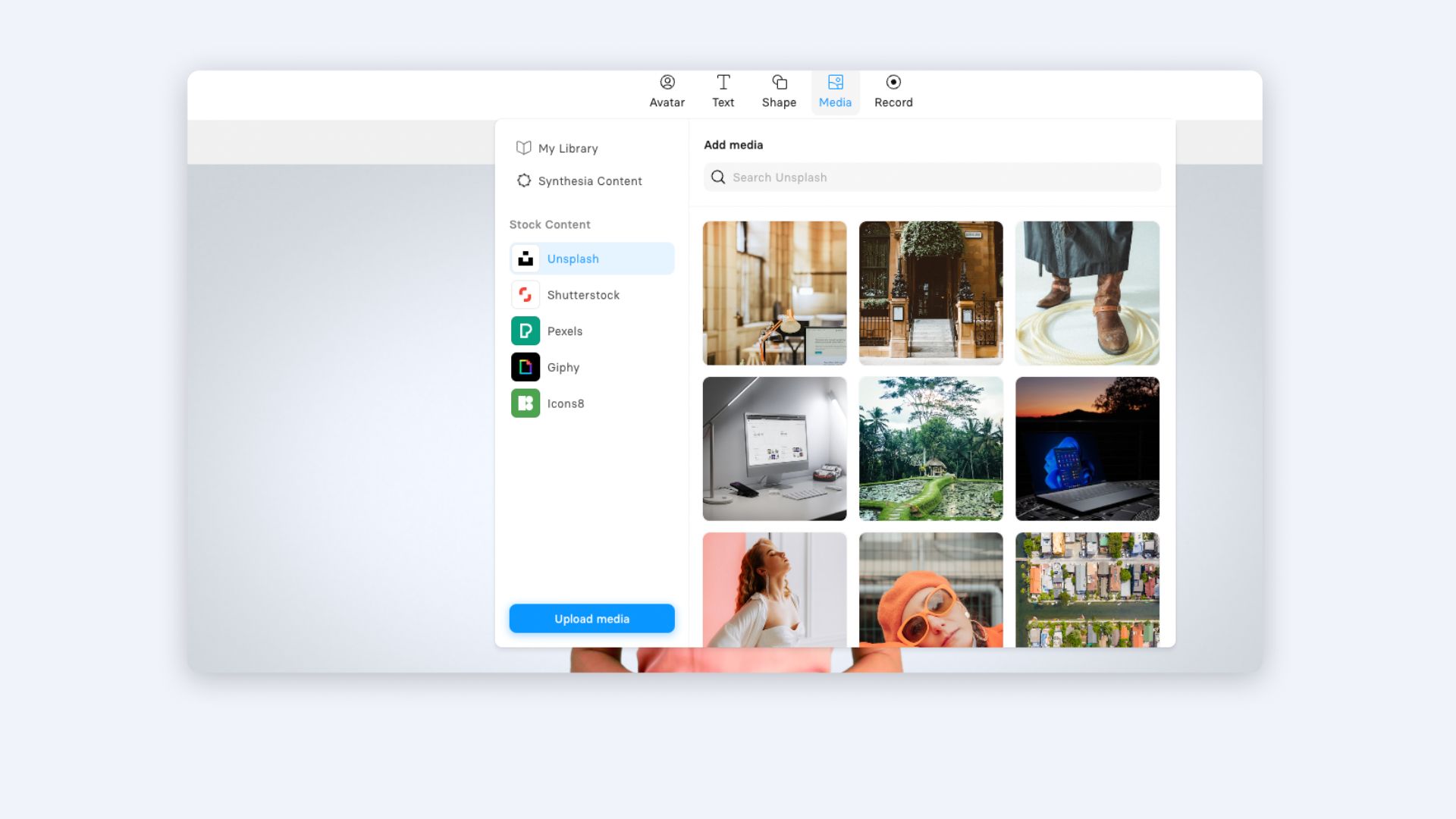
Step 4: Edit your video
The foundation of your video is done, now it's time to personalize it.
The video template is a good starting point, but it's important to customize and change the colors or fonts to fit your organization.
Adjusting timing on animations can help make them align with voiceover narration too!
Here are some of the elements you can add to the video in Synthesia:
- 140+ AI avatars
- stock or own images and videos
- screen recordings
- text on screen
- shapes, shadows, icons, GIFs
- audio
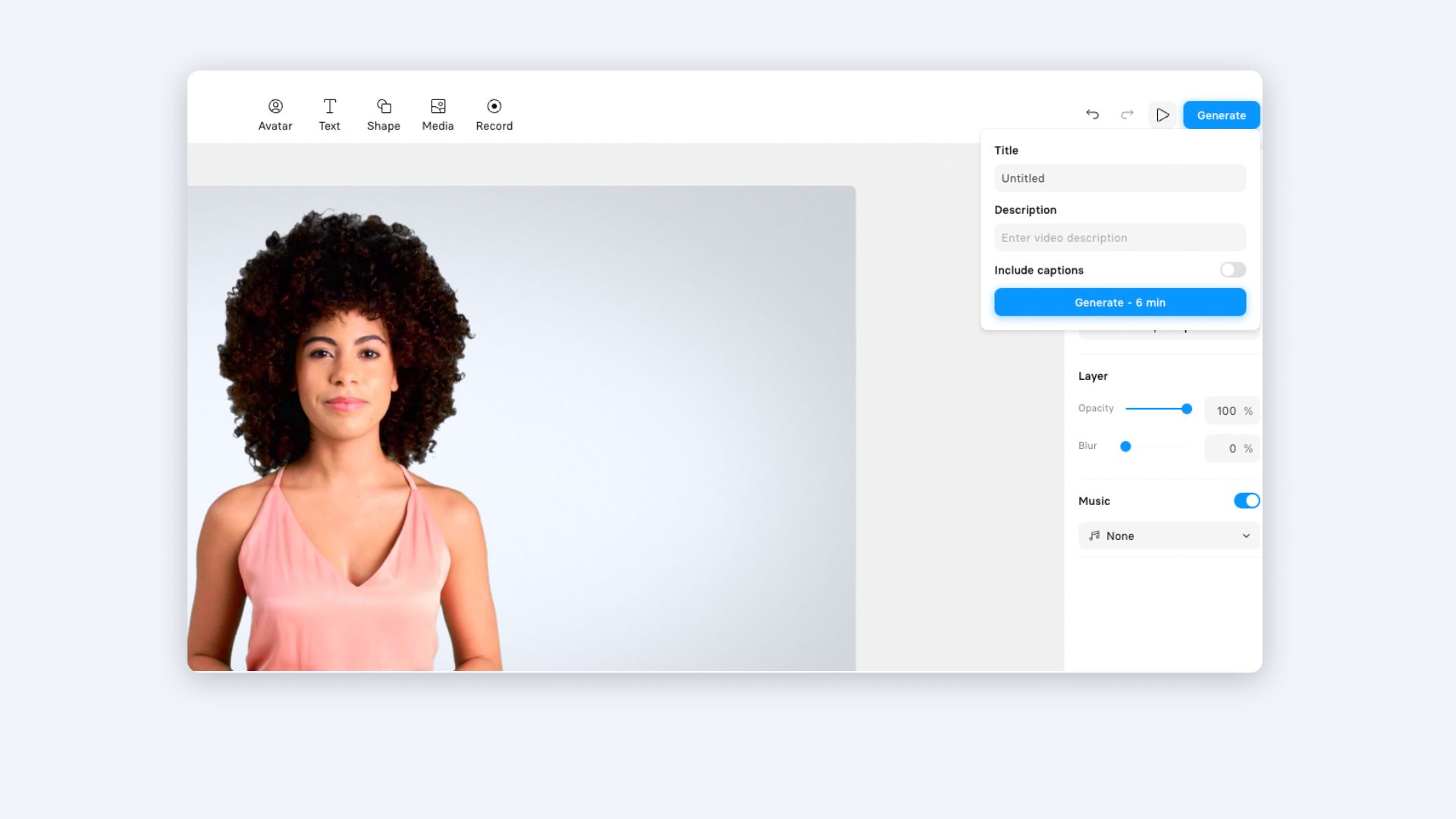
Step 5: Generate video lesson
Your cybersecurity training video is now complete!
After generating the video, you can share the link, download it, or embed it on a distribution platform of your choice.
We have support integrations with some of the most popular LMS/LXPs, so you can track lesson completion and information retention easily.
Protect your business against cyber criminals in a more engaging way...
...by educating your employees with custom cybersecurity training videos.
Now that you know how easy it is to make a cybersecurity training video, there’s no excuse not to get started.
All you need is text, and you can be on your way to creating engaging and informative videos that will help keep your business safe from cyber threats.
Head over to synthesia.io to get started today!
About the author
Strategic Advisor
Kevin Alster
Kevin Alster heads up the learning team at Synthesia. He is focused on building Synthesia Academy and helping people figure out how to use generative AI videos in enterprise. His journey in the tech industry is driven by a decade-long experience in the education sector and various roles where he uses emerging technology to augment communication and creativity through video. He has been developing enterprise and branded learning solutions in organizations such as General Assembly, The School of The New York Times, and Sotheby's Institute of Art.















